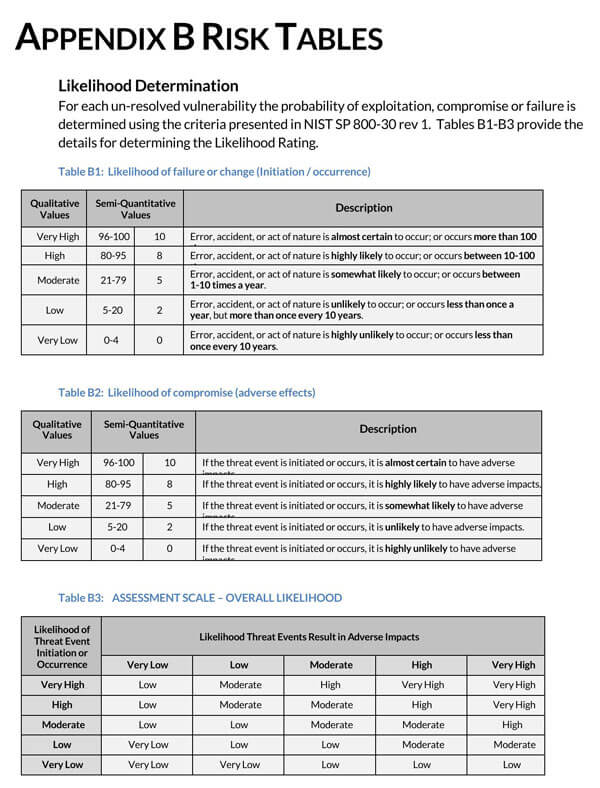
Security assessment reports are a way of ensuring that a company is safe and secure. It is a way of ensuring that an institution is operating at the highest security standards. For that to be possible, you will access the current security structure and identify areas that need improvement. This article seeks to give directions on how you can write a security assessment report.
What is a Security Risk Assessment?
A security risk assessment is a type of evaluation that involves pinpointing the risks in the company’s security system. It seeks to ensure that all protocols are in place to safeguard against any possible threats. Compliance standards require these assessments for security purposes. For example, security firms need them to audit compliance requirements. There are many names associated with security risk assessment — it is also referred to as IT infrastructure risk assessment, risk assessment, or security risk audit.
These assessments are done by certified security assessors who evaluate every aspect of an organization to identify unstable areas. A security risk assessment can be as simple as password checks or unwarranted business processes.
How does a Security Risk Assessment Work?
A security risk assessment assesses, identifies, and implements crucial security controls in a system. The evaluation also focuses on preventing security vulnerabilities and defects. By carrying out a risk assessment, you will view the application portfolio holistically — from an attacker’s point of view.
Here is a step by step explanation of how a risk assessment works:
Start by identifying the problem:
You need to determine all the crucial assets of technology systems. Besides, you should diagnose sensitive data that are manufactured, stored, or transported by these systems. It is essential to create a risk file for each.
An In-depth Analysis of the Problem:
Come up with an approach to assess the possible security risks for vital assets. After a detailed assessment and evaluation, determine how efficiently the system is working, and estimate how much you need to do to secure it. The assessment methodology must analyze the coexistence between vulnerabilities, threats, assets, and mitigating controls.
Preventing further Damages:
This is where you implement processes that reduce threats and prevent potential attacks from occurring.
What Problems does a Security Risk Assessment Solve
The risk assessment will help you identify risks and threats for your system, whether internal or external. This will help the organization to understand the insufficiency and the drawback in the security policies that are there for the organization and will give a list of the threats and risks so that they get a light on how to improve and increase the risk assessment for the security.
A good number of organizations need personal health information when it comes to business operations. This information can come from customers, clients, and partners. Crucial information such as taxi identification, social security number, and driver’s license, date of birth, passport details, and medical history is considered private and confidential.
Listed below are some of the problems that a security risk assessment can solve:
- Establishes a collection of security architecture, network systems, or stored data.
- Develops an asset inventory of physical commodities.
- It creates an app portfolio for all available applications and utilities.
- It documents security requirements, procedures, and policies.
- Maintains information on operating systems.
A comprehensive security assessment allows an organization to:
- Implement mitigation controls for every available asset.
- It helps to identify vulnerabilities.
- It allows you to review your security controls.
- Critically assess the assets on matters to do with business operations.
- Assess the risk ranking for assets and prioritize them accordingly.
What Industries Require an SRA for Compliance?
Assessments play an important role by supporting managers in making informed decisions. They will be able to allocate resources wisely and make better security implementation decisions. Therefore, conducting an assessment is an essential part of a company’s risk management system.
Crucial factors such as resources, growth rate, and asset system can affect risk assessment modules’ depth. As a company, you can carry out generalized assessments when experiencing financial or time constraints. It is important to note that generalized evaluations don’t usually give comprehensive mappings between associated threats, assets, impact, identified risks, and mitigating controls.
Essential Elements of a Security Assessment Report
- The levels of vulnerability
- Applicable threats and their frequency
- The use environment
- The levels of data sensitivity
- System connectivity
- Residual risks
Security Risk Assessment Report Templates
There is a need for a regular security assessment. Using templates is an easy way of writing a security assessment report. Here are some security assessment report templates that are available for download.
Tips to Create a Security Assessment Report
- Prioritize risks and observations: You need to come up with remedies that will fix the problem.
- Create an executive summary: This gives a brief overview of the results of the assessment.
- Analyze data collected during the assessment: This will help you identify relevant issues and fix them.
- Consider submitting a draft first: This weeds out any false positives and fake information.
- Ensure that the report is brief and straightforward.